What Is Malware?

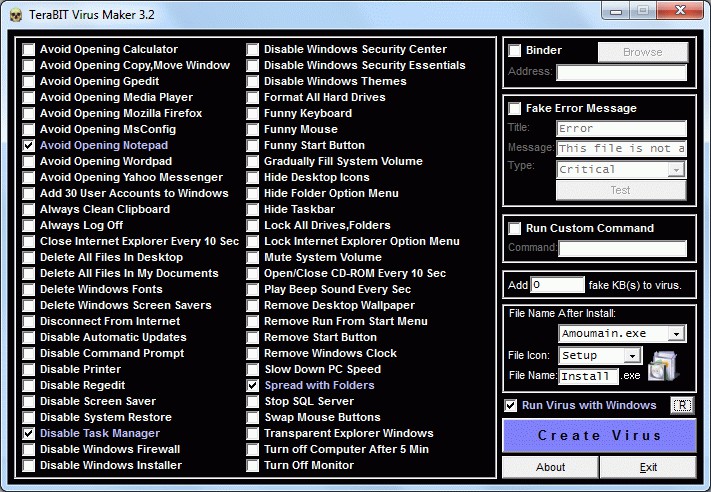
Malware is the name given to various types of malicious software, these include, ransomware, viruses and spyware. Malware is made up with code and is developed by Cyber attackers to either gain unauthorised access to a network or cause an extensive amount of damage to systems and data. This is usually delivered in the form of a link by email and requires the unsuspecting user, ie: you and your staff to click on the link to open and execute the malware. Every week or so we hear of some story of a business that has been the victim of this scourge, no matter how much training or anti-malware software tools you have at your disposal, this still happens on a regular basis. You might be thinking why it is so easy for hackers to create viruses that will inflict so much damage, because there are programs on the internet that can help hackers create viruses easily, some require extensive programming skills while others are relatively easy with interactive graphical programs that help a hacker create a virus, please see the graphic below of TeraBIT Virus Maker below and there are plenty if not hundreds more like this on the internet.
What does Malware do?
Cyber criminals are becoming more and more sophisticated in their methods of delivery to a system and once on your system, the Malware could steal or cause damage to your data or demand a ransom for a code to unlock your data, please see below some common Malware types and definitions.
Virus
This is possibly the most common types of Malware, which is a piece of malicious software that is propagated on to a system through a user’s action, it normally cannot spread by itself and requires a user to initiate it in some way. For example a user may open an infected file or executable, usually viruses are propagated from malicious internet sites or even through removable storage devices like USB drives and then passed on from users to user within an organisation or from computer to computer by transmitting the file via email or file sharing programs.
Crypto-malware or Ransomware
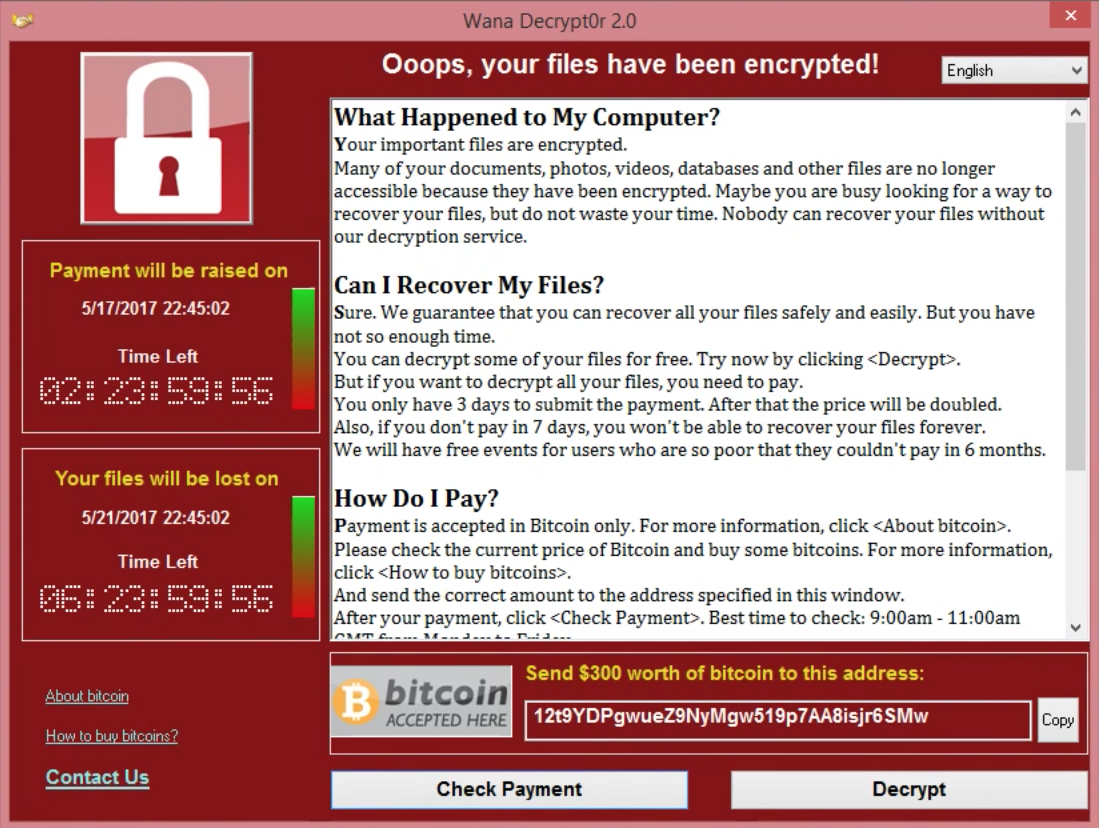
Ransomware is one of the most problematic malwares to date and are often impossible to disinfect. Crypto-malware uses a form of encryption to lock a user out of a system by encrypting the boot drive and files on a computer or system and the attacker will demand a ransom to be paid for the decryption of the system or files – See graphic below of a Ransom notification
Worm
It is much like a virus and can cause disruptions to the host and slow a system down and then spread itself throughout a network by self-replicating and infecting an entire network and requires very little user intervention.
Trojan Horse
This named after the Greek mythological story of the trojan horse and this type of malware gaining access by means of a useful piece of software to the user or in the form of a game and its main goal is to collect personal information, including users credentials and financial information.
Keylogger
This is a piece of malware that can record keystrokes by a user. The keylogger will store a certain number of keystrokes in a file and then send them to the bad actor, who can use this information usually with collected passwords and usernames by an unsuspecting user
Rootkit
This is a piece of malware that attempts to infect operating system files on the host machine and usually an Antivirus program cannot detect a rootkit easily so it can live on a system for quite a while without being detected.
Spyware
This is used for the specific purpose of observing a user’s actions and then recording it, also for stealing sensitive information like passwords and credit card details without the user knowing.
Bots/Botnet
This is a distributed type of malware attack that uses remotely controlled malware that has infected multiple computers on a network. Once the malware is installed on a host the attacker can control the hosts remotely and send malicious commands to be carried out.
Logic bomb
This is usually a script set to execute at a time or if certain events or circumstances take place on a system. It is designed to take malicious actions like erasing files from a storage disk on a certain time or date. Logic bombs are normally the result of an insider like a disgruntled network administrator who has fallen out with the boss.
How to protect yourself
There is no magic silver bullet, but employee education and training is absolute key to make your users aware of the risks of malware and what they can do to prevent it. With good policies in place and the right ant-malware solutions that can monitor your network, malware will stand less of a chance of being a problem for your business.
What to do next
-
If you are thinking about changing your current IT Service Provider or are looking for some good anti-malware and cyber security solutions for your business, get in touch here or phone 01738 310 271
-
Want to know more about what to expect from a Managed IT Service Provider – click here